Big Data Security: Strategies to Protect Your Business Data
Today, keeping big data security safe is very important for businesses, whether they are small or large. When data is stolen, it can hurt a company’s money and reputation. This can make customers lose trust in the company. It is vital to understand how to protect data well. This article will give you some easy steps to improve big data security. Implementing efficient big data security measures is essential to safeguard sensitive information. Implementing effective data breach prevention strategies is crucial for maintaining customer trust.
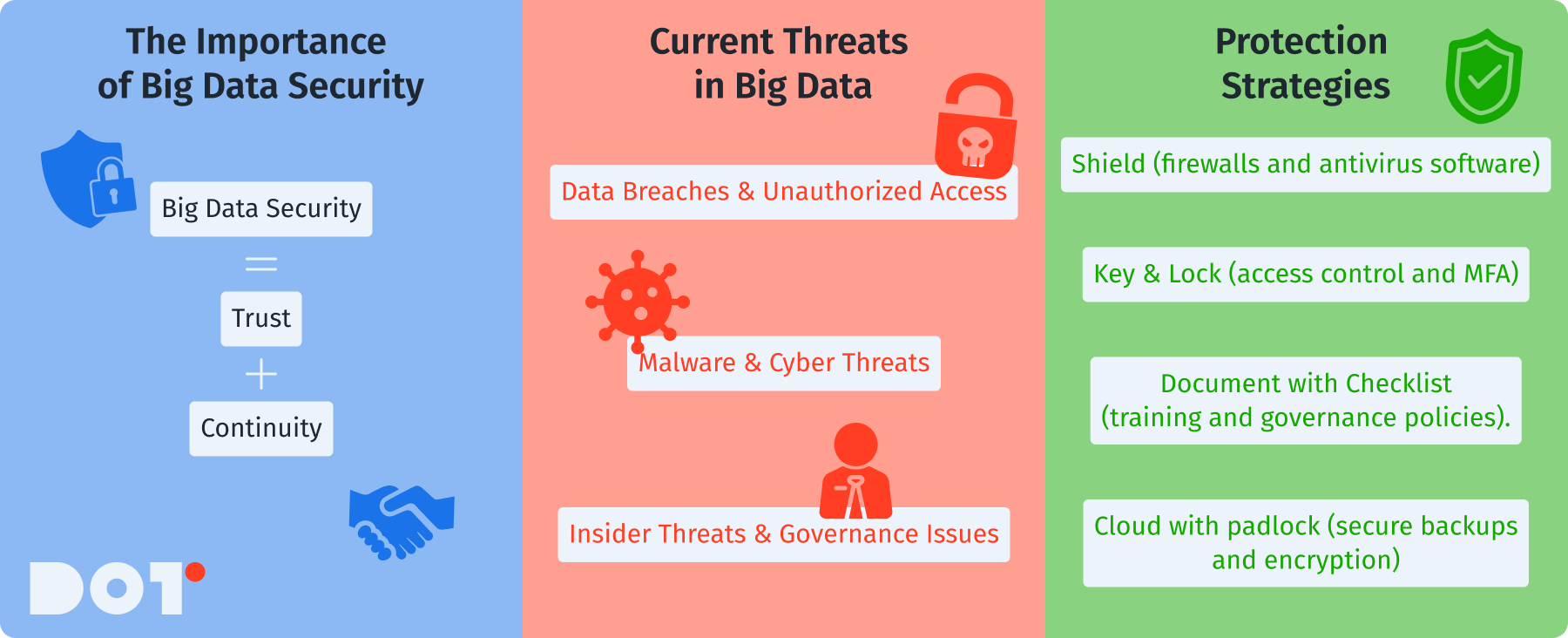
Recognizing the Significance of Big Data Security
Big data security is very important for companies today. Businesses gather lots of data, from employee information to customer details. This data is valuable, but it can also be dangerous. If this data is protected well, it can help make better business choices, improve marketing, and create better customer experiences. But if this information is not safe, it can lead to serious problems like losing valuable ideas, breaking laws, and harming the company’s reputation. Effective big data security strategies can minimize the risk of such threats. Understanding big data privacy measures allows organizations to ensure compliance and build customer confidence.
Cybercriminals are always looking for weak spots in data systems, and they can take advantage of unprotected databases. Research shows that about 60% of small businesses close their doors within six months of a data breach. Knowing how important big data security is means understanding that it helps keep businesses running and builds trust with customers. To ensure continued success, organizations must prioritize big data security in their operational frameworks. Investing in cybersecurity for big data helps protect sensitive information from threats.
The Current Environment of Big Data Risks
The digital world today has many risks for businesses using big data. Hackers can use very smart methods to get into company systems. With more people working from home, it has become easier for attackers. Employees may access sensitive data using devices that are not secure or on public networks. As part of a comprehensive strategy, big data security must address these vulnerabilities effectively. Implementing robust data encryption techniques is essential in securing data both at rest and in transit.
Besides outside dangers, problems from within the company also exist. Sometimes employees can accidentally put data at risk by not following security rules. With more companies using cloud services, there can be more risks because they may not have complete control over their data once it leaves their offices. Investing in big data security is essential for maintaining a robust defense against both external and internal threats. The understanding of risk management in big data can significantly enhance security protocols.
Data protection rules are getting stricter. Businesses must follow regulations like GDPR and CCPA, which require careful data handling. If a breach happens, it may lead to big fines and loss of customer loyalty. All these challenges show that strong security measures are necessary for big data. Awareness of big data compliance frameworks can help organizations navigate legal obligations.
Common Security Risks Linked to Big Data
Data Breaches and Unauthorized Access
Data breaches happen when people not allowed to access sensitive information manage to do so. Cybercriminals use different methods like phishing emails or social tricks to steal information. For example, they may trick an employee into giving up their login details, which allows hackers to break into the system and steal confidential data. It can be very hard for even big companies to recover from such events, as seen with the Target and Equifax breaches. Incorporating comprehensive big data security into their operations can help companies safeguard against these types of incidents.
To stop unauthorized access, you can use strong access control methods. Consider using multi-factor authentication (MFA), strict access guidelines, and keep logs of who accesses what data and when. Tools for preventing data loss can help watch for unusual activity on devices. Implementing security analytics solutions can help detect potential breaches before they escalate.
Malware and Cyber Threats
Malware is getting more complicated and can harm big data systems. Ransomware attacks are particularly dangerous because they lock important data and demand payment to unlock it. This can stop businesses from working normally and cost a lot of money. Enforcing big data security protocols is critical to mitigating the impact of malware attacks.
To reduce malware risks, start by training employees on how to avoid suspicious links and attachments. Many malware infections come from mistakes made by people. Also, use strong antivirus software, properly set up firewalls, and regularly update software to fix vulnerabilities. Regularly back up data in safe places to lessen the damage from a ransomware attack.
Insider Threats and Ineffective Data Governance
Insider threats can be very damaging. They happen when employees either intentionally harm the organization or accidentally expose data due to lack of knowledge. Studies estimate that about 30% of data breaches come from insider threats. This shows the importance of having good data governance to track who accesses what information and how it is kept safe. Enhancing big data security includes focusing on effective data governance to address insider threats.
To strengthen data governance, put rules in place that define who can access what data, like role-based access controls (RBAC). This ensures that employees can only see the information they need for their jobs. Also, ongoing employee training about data privacy can help create a culture that values security.
Evaluating Existing Security Measures
Performing a Risk Assessment
To check your current security measures, conducting a risk assessment is a key step. Here’s how to do it:
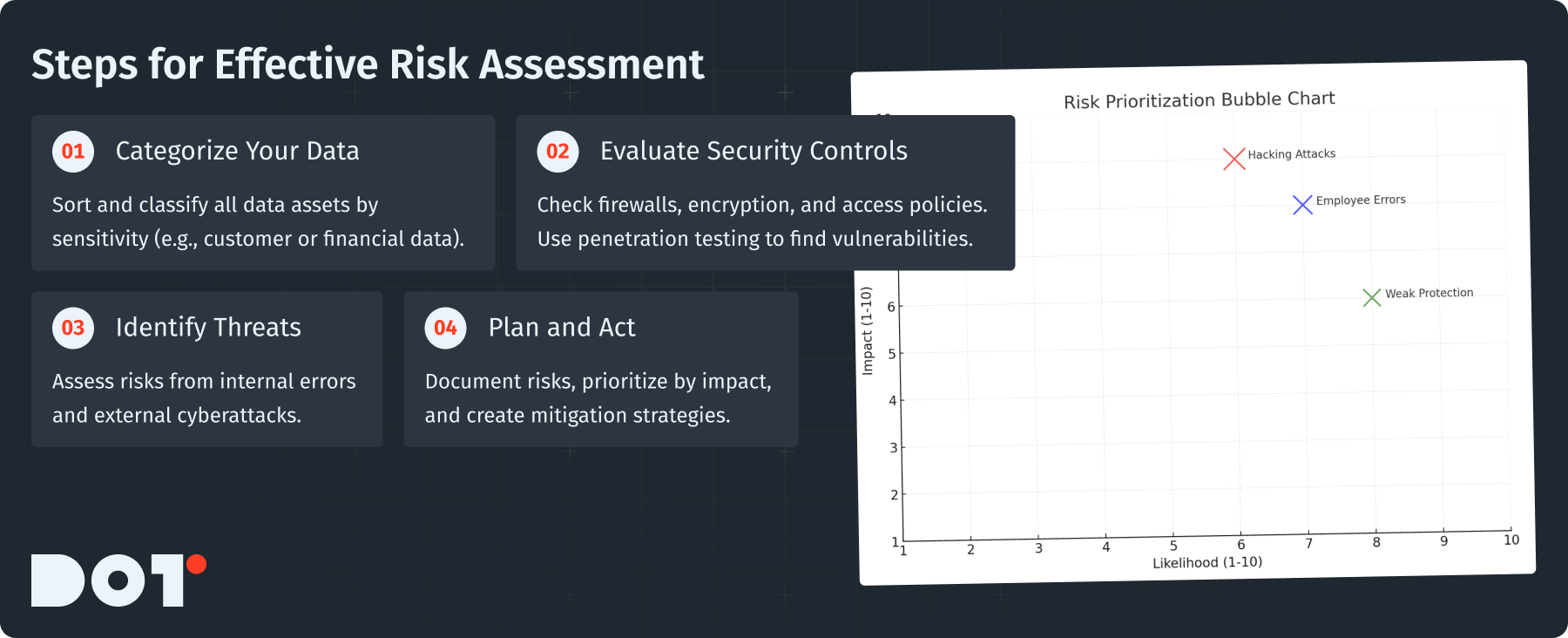
- Identify and categorize data: Make a list of your data assets and sort them by how sensitive they are. This might include employee data, customer details, or financial information.
- Assess current security controls: Look over the existing protections for your data. Are firewalls, encryption, and access controls working well? Use penetration testing to see how easily an outsider could find weaknesses.
- Identify potential threats: Think about the different inside and outside threats that could harm your data. This includes employee mistakes and advanced hacking methods.
- Document findings and develop a plan: Write down what you find and prioritize the risks based on their possible impact. Then, create a plan of actions to reduce these risks.
Make sure to review this assessment regularly to keep your security strong as new risks come up. Continuous adjustments based on the risk assessment can enhance your big data security.
Reviewing Current Security Protocols
Next, check the current security protocols you have. Start by looking at these:
- Encryption practices:
Is your data encrypted when stored and when being sent? Check for outdated methods and ensure you use strong encryption standards (like AES-256) to protect sensitive data.
- Network security measures:
Are firewalls set up correctly? Make sure to regularly review firewall rules to block unwanted traffic.
- Access control policies:
Check if your access control methods (like role-based access and time-based access rules) are in place and if anyone has access who shouldn’t.
This review should not just happen once; make it a routine part of adapting to the changing digital world with a focus on big data security.
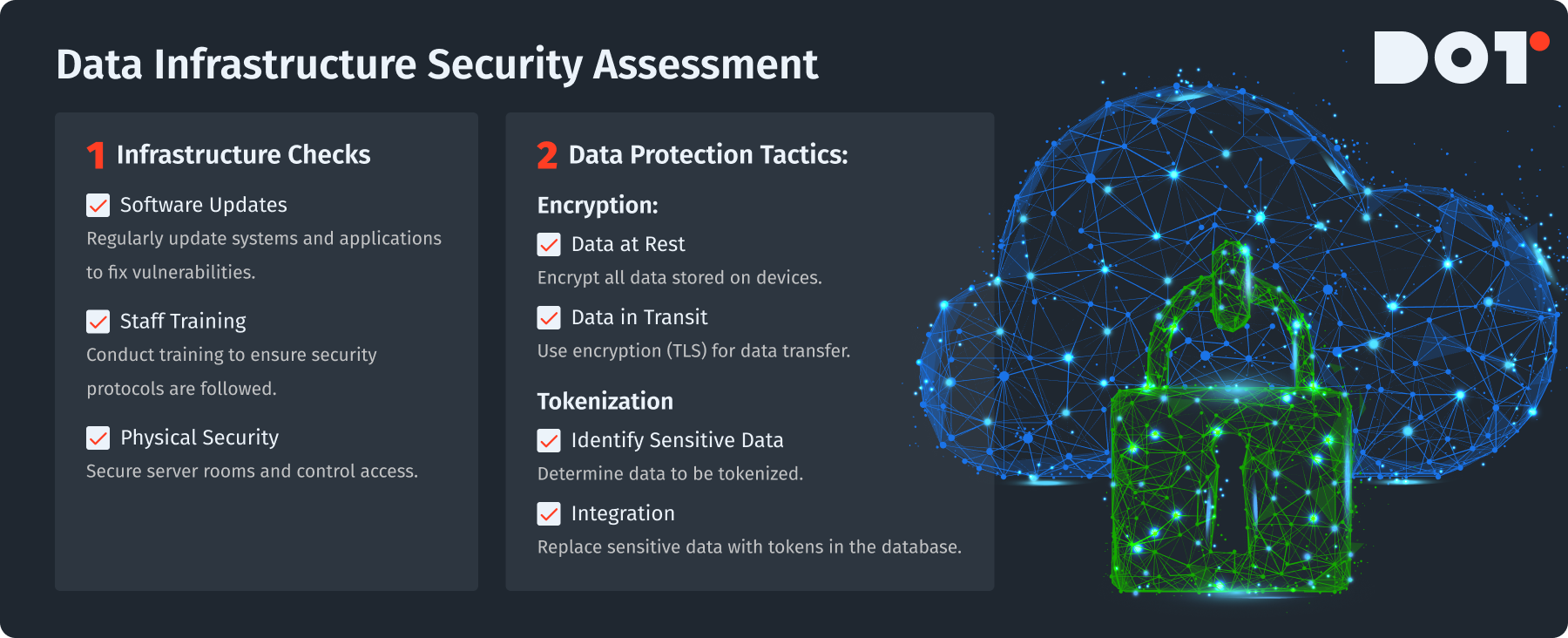
Spotting Vulnerabilities in Data Infrastructure
Regularly examining your data infrastructure is important to find weaknesses. Make these checks:
- Software updates: Make sure all your software, including operating systems and applications, is updated to the latest versions that fix known issues. Keep a schedule for regular updates.
- Staff training: Ensure that workers always follow security rules. Regular training can help everyone understand the importance of secure data handling.
- Physical security assessments: Check how people access your data infrastructure. Keep server rooms secured and track who enters these areas.
By frequently looking for vulnerabilities, you can manage risks proactively instead of reacting after problems occur. Making big data security a priority in these assessments will ensure thorough protection.
Tactics to Safeguard Sensitive Data
Utilizing Encryption and Tokenization
Encryption is a very effective way to protect sensitive data. Here’s how to use it well:
- Encrypt data at rest:
Use encryption techniques on all places where sensitive information is stored. This ensures that even if attackers get access, the data remains unreadable without the keys to unlock it.
- Encrypt data in transit:
Use Transport Layer Security (TLS) to encrypt data sent over the internet. This is important when information moves between points, especially when networks are not secure.
Tokenization provides an extra layer of protection. It replaces sensitive data with a non-sensitive token. This means that even if hackers get to the data, it won’t help them at all. To use tokenization:
- Identify sensitive data: List what data you want to tokenize.
- Select a tokenization provider: Pick a service that offers tokenization that works with your current systems.
- Integrate tokens into your database: Change your database to replace sensitive data with tokens, while keeping the option to revert back when needed.
By using both encryption and tokenization, you can set up strong defenses against unwanted access that enhance your big data security.
Implementing Access Controls
Access control is more than just limiting access to sensitive information; it’s a complete strategy:
- Role-Based Access Control (RBAC):
Assign roles to workers based on what their jobs are. Each role should specify what data is needed. For instance, a marketing worker may not need access to payroll information.
- Principle of Least Privilege:
Make sure employees only have access to the data they need. Regularly review and adjust permissions as jobs change.
- Implement a re-access policy:
Regularly check access permissions, especially when workers change roles or leave.
- Session timeouts:
Set time limits on how long users can stay logged into the systems. This helps if someone leaves their computer unattended.
By being careful with access controls, you provide a key security layer that can greatly lower the chances of data breaches, reinforcing your big data security strategy.
Continuously Updating Security Policies and Procedures
Having a static security policy is not strong enough. To keep your organization safe from new threats:
- Regularly review security policies: Have someone in charge of reviewing data security policies every year. This should consider new threats and learnings from past data incidents.
- Employee feedback loops: Talk to employees about security policies. Get their feedback to identify real challenges with security measures.
- Establish incident response protocols: Write down steps the organization should take if a data breach happens. Train employees on these protocols and practice through simulations.
- Foster a culture of security: Regularly remind employees about the importance of security through newsletters, training, and discussions in team meetings.
By keeping security policies active and relevant, you significantly improve your organization’s ability to handle threats related to big data security.
If this topic is top of mind for you, book a free 20-minute consultation with a Dot Analytics expert.
Essential Tools and Software for Big Data Security
Overview of Key Security Tools (e.g., Firewalls, IDS/IPS)
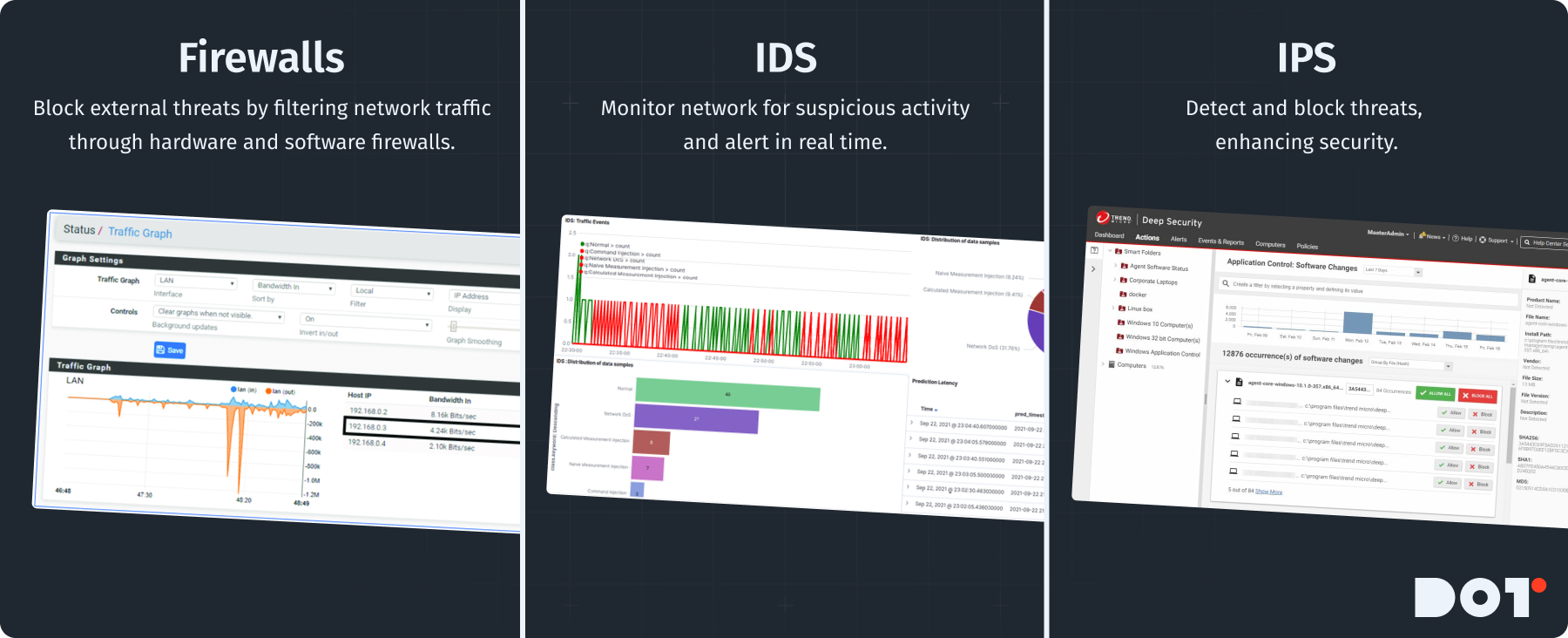
Having the right tools is essential for good data security. Start with firewalls:
- Firewalls:
These act as a wall between your network and outside threats. Set up both hardware and software firewalls to filter traffic in and out of your network.
- Intrusion Detection Systems (IDS):
IDS watch your network for suspicious actions and alert you in real time. When paired with your firewall, they make security stronger.
- Intrusion Prevention Systems (IPS):
These systems not only find threats but also stop them, giving even better security. Implementing these tools is a critical part of maintaining big data security.
Other tools like Security Information and Event Management (SIEM) systems collect logs and alerts, helping you monitor threats on your network. Incorporating security analytics solutions into your strategy can enhance overall monitoring capabilities.
Comparing Software Solutions for Data Protection
Choosing good software for data protection is key for solid big data security. Start by comparing popular products:
- Symantec Endpoint Protection:
Offers solid malware protection and tools to prevent data loss.
- McAfee Total Protection:
Provides strong security features for finding and reducing threats, plus it has encryption tools.
- Splunk:
Known for its analytics, it can be customized for security monitoring, giving insights from many sources.
When comparing options, check how well they work with your current systems, and consider ease of use, support, and user feedback to find the best choice for your organization, always keeping big data security in mind.
Integrating Security Tools with Big Data Platforms
Making sure your security tools work well with big data systems is crucial:
- API integrations:
Use Application Programming Interfaces (APIs) to let your security tools communicate with your data systems. You may need IT skills for this, so check with your tech team.
- Monitor data workflows:
Ensure your security tools can oversee all data transactions in your big data systems for real-time alerts on suspicious actions.
- Regular training:
Give sessions to educate employees about how to use these connected systems to get the best out of security tools.
By connecting security tools properly, you can enhance data protection in a way that strengthens your big data security framework.
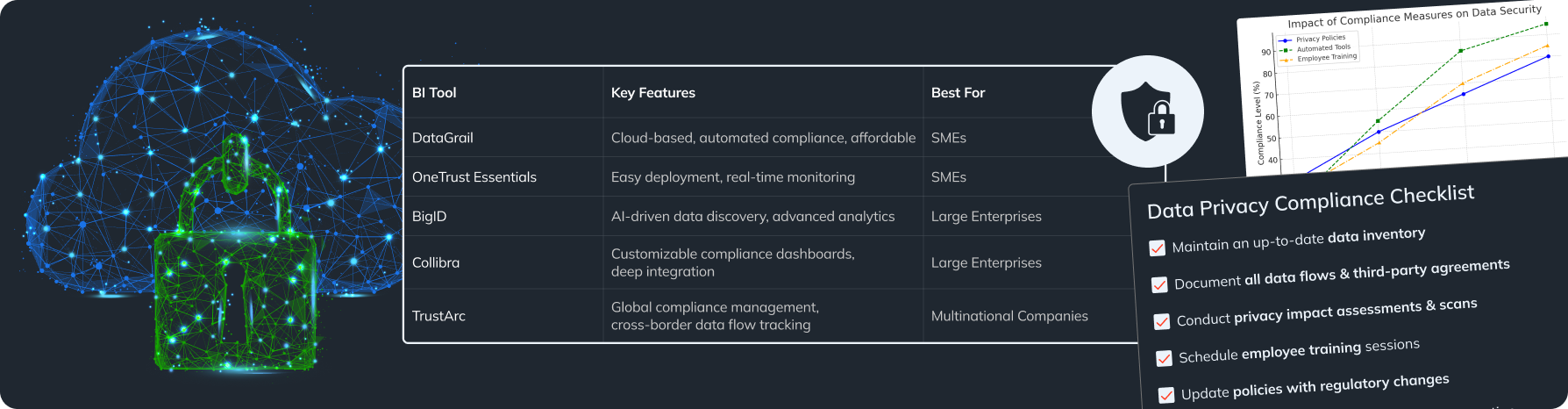
Meeting Compliance with Data Protection Regulations
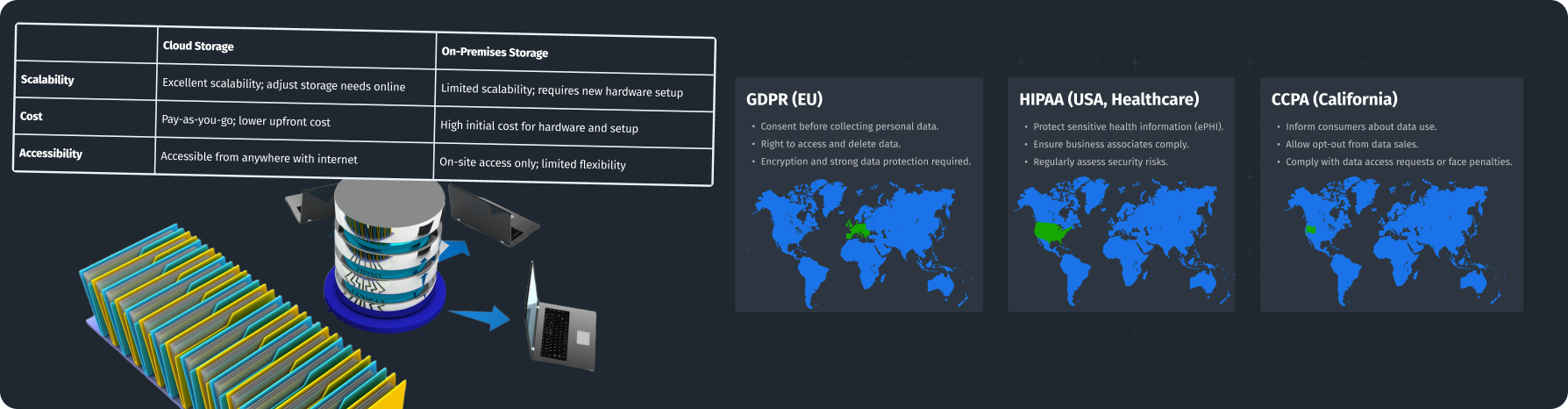
Understanding GDPR and CCPA Requirements
Knowing regulatory rules is very important for handling data in a compliant way. The General Data Protection Regulation (GDPR) is for data protection and privacy in the EU, while the California Consumer Privacy Act (CCPA) does the same in California.
- Data subject rights: Both rules give people rights regarding their data, like the right to access, correct, or delete their information.
- Consent: Make sure your company asks for clear permission before collecting personal data and keeps records of these permissions.
- Data breach notifications: Under GDPR, organizations must inform authorities within 72 hours of a breach, while CCPA requires notifying consumers quickly.
Understanding these regulations helps you reduce the risks of non-compliance and keeps your organization safe from fines. Ensuring that big data security measures align with these regulations is fundamental for compliance.
Applying Data Stewardship Practices
Strong data stewardship practices need teamwork across departments. Here’s how to do it:
- Define ownership:
Choose data stewards in departments responsible for data quality and safety. They should oversee data access and compliance.
- Create policies and procedures:
Write down best practices for managing data, how long to keep it, and how to delete it, making sure these rules match regulations.
- Employee education:
Hold regular training to help workers understand data stewardship and their roles in safeguarding data.
- Technology adoption:
Use data management tools that help enforce rules and show how data is being used.
By having good data stewardship practices, you help ensure compliance and build a culture that values data integrity as part of your big data security strategy.
Conducting Regular Compliance Audits and Reports
Regular audits are key to making sure your organization follows data protection rules. Here’s how to do this well:
- Define audit parameters: Set clear goals for your audit, checking compliance with GDPR, CCPA, and internal rules.
- Gather documentation: Collect documents related to how data is processed, consent records, and data access logs for review.
- Analyze findings: Look for discrepancies and areas for improvement. Create a report detailing findings, risks, and ways to enhance security.
- Implement corrective actions: Develop a system to track how recommendations are acted upon within a reasonable time.
Regular audits help you stay compliant and fix issues before they become big problems, reinforcing your commitment to big data security.
Do you fully understand the topic? If not, you can book a free 15-minute consultation with an expert from Dot Analytics.
Education and Resources for Team Training
Identifying Best Practices in Big Data Security
Organizations need to set best practices for data security and ensure all employees know these rules. Some best practices include:
- Keeping software updated: Regular updates help fix vulnerabilities.
- Fostering secure password policies: Have rules for strong passwords and regular updates.
- Reporting incidents: Set up simple ways for workers to report suspicious activities.
By communicating these best practices clearly, your organization can build a stronger security culture dedicated to big data security.
Online Training Programs and Workshops
Training teams through online programs or workshops can help improve awareness of data security:
- Identify suitable platforms:
Research platforms like Coursera or Udacity that offer courses on data security.
- Corporate training programs:
Some companies create tailored training for specific needs. Look for programs focusing on big data security and compliance.
- Certification courses:
Encourage team members to get certified in areas like Certified Information Systems Security Professional (CISSP) or Certified Information Security Manager (CISM).
By focusing on ongoing education, you empower your team to make significant contributions to data security while enhancing their understanding of big data security.
Fostering a Culture of Security Awareness
Creating a security-awareness culture can help protect your data:
- Regular meetings: Hold discussions on security updates, new threats, or changes to policies to keep awareness high.
- Incentivize security: Consider rewarding employees who help protect data or report threats.
- Create awareness campaigns: Launch initiatives highlighting best practices like “Phishing Awareness Month” to educate staff.
- Leadership involvement: Ensure leaders talk about security and set a good example of data stewardship.
These actions promote a proactive approach to data security across the organization, with big data security as a fundamental aspect.
Case Studies on Big Data Security Implementation
Galleri5: Enhancing Data Protection in Influencer Marketing
Company Overview: Galleri5 connects brands with influencers to create engaging marketing campaigns. They handle a lot of sensitive customer data.
Challenge: They needed to protect sensitive data while keeping the user experience friendly and easy. They needed to improve data protection to keep clients’ and influencers’ trust.
What They Did: They created a strong encryption strategy and improved their data governance rules for better access and monitoring.
How They Did It:
- Team Composition: A team with 5 IT security experts, 2 data analysts, and 1 compliance officer was formed.
- Training Initiatives: They held workshops for staff to teach them about new rules and practices.
- Technologies Used: They used AWS encryption services and Splunk for real-time security monitoring.
Results: Within the first six months of these changes, Galleri5 saw a 60% drop in data breach attempts, which improved clients’ confidence in their data handling, leading to more business. Their enhanced focus on big data security contributed directly to these positive outcomes.
InfluxCrowd: Securing Data Across Marketing Platforms
Company Overview: InfluxCrowd is focused on influencer marketing, helping brands connect with influential people.
Challenge: They faced risks from clients who shared sensitive data that could be targeted by cybercriminals.
What They Did: They implemented multi-factor authentication (MFA) for access and upgraded their firewall systems.
How They Did It:
- Team Composition: Their team included 4 cybersecurity analysts, 3 marketing specialists, and 2 external consultants for expert guidance.
- Simulations for Training: They performed regular simulations to prepare employees for potential security breaches.
- Technologies Used: They used Cisco firewalls, Google Authenticator for MFA, and created custom training software for staff.
Results: InfluxCrowd achieved a remarkable 70% reduction in successful phishing attacks and improved response times by 40%, significantly bolstering their overall big data security posture.
Checklist for Big Data Security
Key Security Controls to Implement
- Regular updates and patches:
Create a schedule to keep all software current, answering vulnerabilities as they are identified. - Access Controls:
Set clear access rules to limit data access to authorized personnel only. Use role-based access where it makes sense.
Ongoing Monitoring and Reporting Practices
Make continuous monitoring and regular reporting a habit for all data activities in your organization:
- Automated Alerts:
Use systems that alert you to unusual data activities or access patterns.
- Monthly Reports:
Create monthly summaries of data access and note security issues for stakeholders.
New Developments in Big Data Security
Emerging Technologies and Their Impact
Technology is quickly changing big data security. AI and Machine Learning are helpful in spotting and responding to threats, making it faster to find and fix issues. By using these new technologies, organizations can tell if user behavior is normal or if there is a potential risk. Implementing big data security measures should include leveraging these technologies for enhanced protection.
- AI-Powered Security Solutions: Look for AI tools that can analyze large amounts of data to find vulnerabilities early.
- Automated Incident Response: Using machine learning can help companies create proactive responses based on the likelihood of threats.
Future Trends in Data Protection
There are promising trends in data protection to watch for:
- Increased Regulation: As cyber threats change, data protection laws will evolve too. Stay informed and compliant.
- Decentralized Solutions: Technologies such as blockchain can help keep data safe and authentic, providing a permanent record of all data activities.
Keeping an eye on these trends will help businesses know which technologies and strategies to invest in for better data security, aligning with overall big data security objectives.
Summary
Recap of Key Strategies
To keep your business data safe, understand the importance of big data security, check for threats continuously, review what security measures you have, and use advanced tactics like encryption and access controls.
Final Thoughts on Implementing a Security Framework
Moving forward, businesses need a complete security plan that matches their specific data management needs. Conduct regular reviews and updates to keep best practices in place regarding big data security.
Next Steps for Businesses
Find areas where your organization can improve its security protocols right away. Start with risk assessments and targeted training programs. These steps will help create a safer data environment, enhancing your big data security strategy.
Want to see how this applies to your business? Schedule a free 20-minute consultation with one of our experts. Our team at Dot Analytics is here to help you navigate big data security efficiently and effectively.













Leave a Reply